This is the 3rd blog post of the OAuth series, and I have already completed the numbers 2 and 4. Once I complete this blog post today (Hopefully), I only have one to write. I will try to complete that one also within next week when I find some time during the night.
I have been using Azure Logic Apps heavily for the past few years while building different integration solutions to connect Microsoft Dynamics 365 Business Central with other third-party applications. In all of these implementations, I used Basic Authentication with Business Central. Web Service Key of the Business Central User and the User Name was stored in the Azure Key Vault as a secret. Logic App retrieves the secrets during the runtime using the Key Vault connector or using Key Vault API. These retrieved secrets are passed to Business Central to authenticate the API requests.
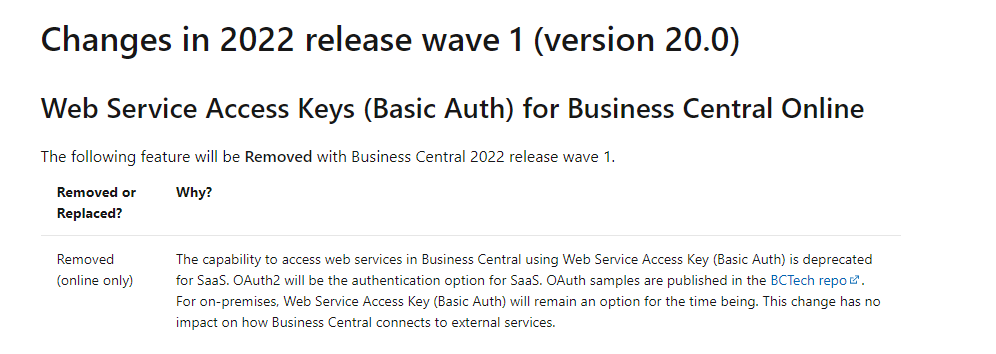
After the 2022 Wave 1 release, we will not be able to use the Basic Authentication with Business Central as Microsoft is going to depreciate the Basic Authentication with Web Service Key for the cloud version of the Business Central.
I have written a series of blog posts about the new OAuth authentication we have to use to connect to Business Central going forward.
This blog post will show you how to use OAuth to connect to Business Central from Azure Logic Apps. Before we go ahead and talk about how to use OAuth to connect to Business Central from Azure, you need to complete a few steps. Please click here to read about what you need to do before starting to change your Logic Apps to use OAuth.
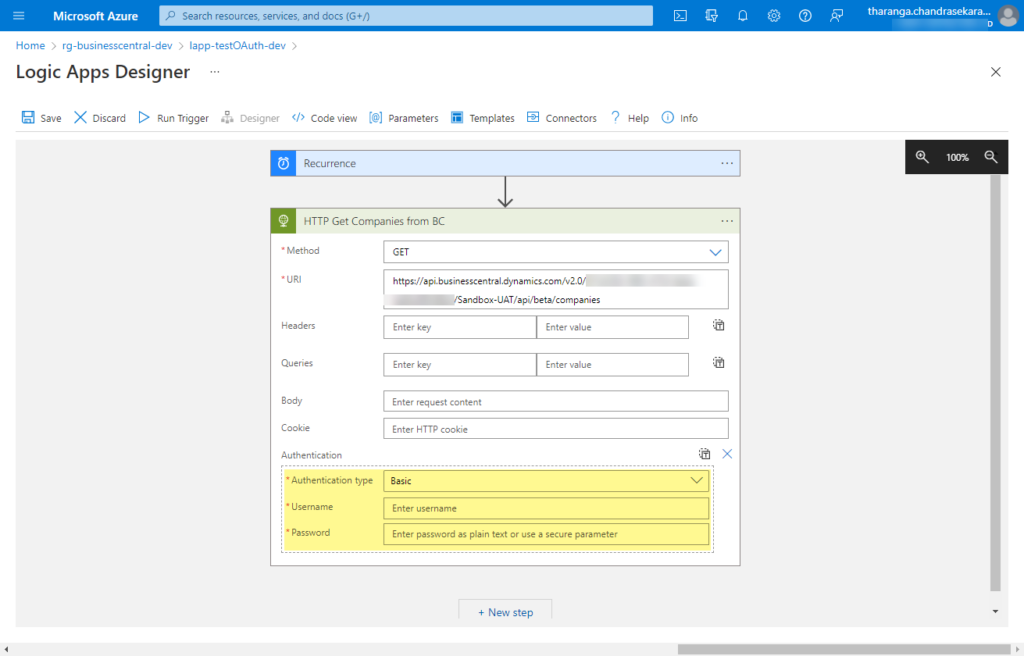
Once you complete the app registration and grant permission in Business Central, now you need to change the Azure Logic Apps. If you open up your Logic App and go to the HTTP connector that calls the Business Central API, you’ll notice that the “Authentication type” is set to Basic and with that, you can only pass the Username and Password.
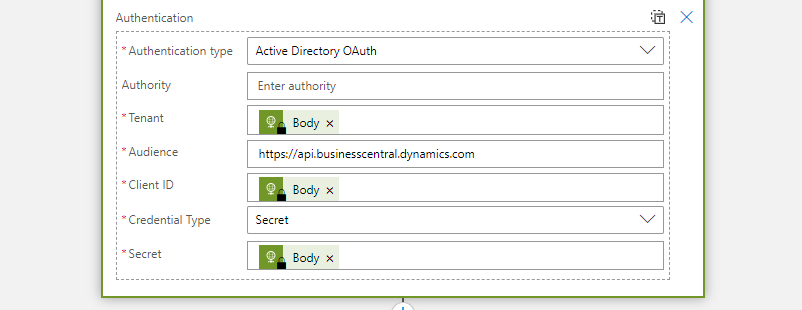
In order to use OAuth on the HTTP connector, you should select the”Active Directory OAuth” as the “Authentication type”. Once you select the “Authentication type” as the “Active Directory OAuth” you will notice 6 new fields appears under the Authentication. Each of these fields needs to be filled correctly to have a successful authorization.
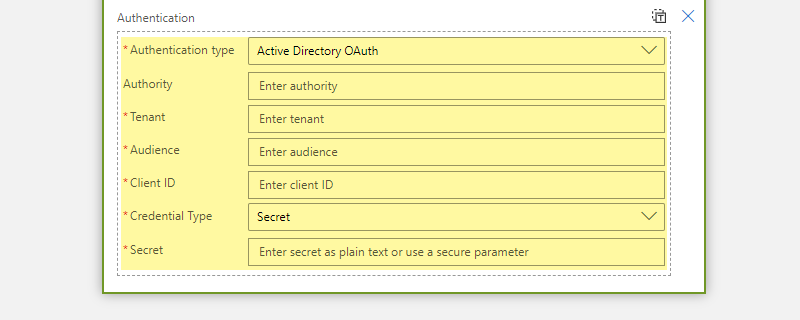
- Tenant: Business Central Teant ID
- Audience: https://api.businesscentral.dynamics.com/
- Client ID: Application ID of the application we registerd in Azure Active Directory
- Credential Type: Secret
- Secret: Secret value we created in the Application
** In order to understand how to get the Client ID and Secret, please read my blog post “OAuth – Part 02 – Configure Service to Service Authentication“
Once you provide all the values, your Logic App HTTP connector should look like below:
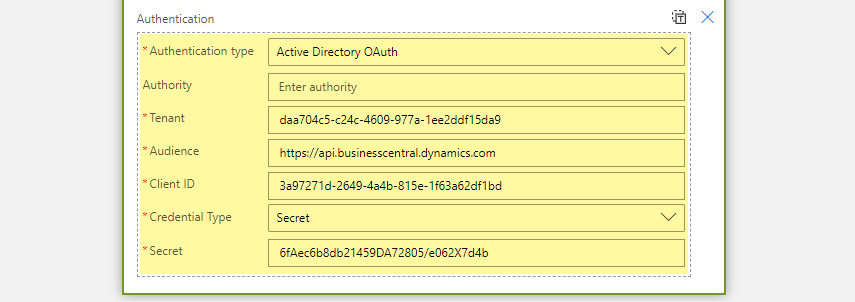
In the above screenshot, Tenant ID, Client ID and Secret are made up values to demonstrate how it should look like and you should use your own tenant values.
In the previous screenshot, all the secrets and other Authentication related values are in plain text and it is an extremely bad practice and put the entire system at risk. I have only done that to take a screenshot so that you will have a better understanding of what kind of values you should put into each field.
The best practice is to store all the secrets and other values in the Azure Key Vault and then retrieve those secret values using the Key Vault connector or through Key Vault API. Then those retrieved values can be used to fill the Authentication fields. Once you do that your HTTP connector will look like below.
Good luck with the changes and if you have any other questions, please feel free to send them to me on Twitter or post them here.
Thank you and Regards,
Tharanga Chandrasekara

